What is Penetration Testing? A Quick Guide for 2025
Computer security has never been more important. With hackers threatening your bank account, ransomware that can shut down your PC if you don’t pay the asking price and everyone spying on everyone else, it is fair to say the security picture is more complex than ever before.
Fortunately, not everyone with security skills is out to get you. Some hackers work for good, probing for vulnerabilities with the goal of fixing them rather than exploiting them for personal gain.
In this article, we’re going to look at their role and explain what penetration testing is.
But First: Black Hat vs White Hat

The good guys are commonly known as white hat testers. The bad guys are black hats and the gray hats are somewhere in between. If you saw any of them working, they would mostly be doing the same thing: checking websites for vulnerabilities. The difference is what happens when they find an issue.
White hats report the issue to the owner of the website or application. Black hats are looking to hack into the website or sell information about the exploit to others. Gray hats don’t quite fit those categories. They might hack for fun or curiosity, potentially breaking the law, but not looking to make money or do harm.
Why Web Application Security Matters
Anyone with an online presence can be hacked. Your neighbor’s Twitter account and international banks are both targets. The rewards for breaking into a website can be limitless.
If a website is compromised, the hacker can take anything from usernames and passwords to credit card details or medical records. Most of us know someone whose email has been hacked, often sending messages to everyone in their contact list, so cybercrime is having an impact on us all.
Once hackers have control of a website, they can use it to steal more customer details, which can be used to access bank accounts or steal bitcoin. They may also be able to get confidential business or technical information.
Naturally, companies are keen to do anything they can to prevent security breaches. Hiring a penetration test, or pentest, specialist is a great way to help them get the edge over hackers.
A vulnerability assessment by a security professional involves hiring someone to attempt to break into the website. They can probe for security holes in the same way a criminal would and report problems they find to the website owner, who can then have them fixed.
Vulnerability Assessment

New weaknesses in software and websites are constantly being discovered. The latest software versions usually include fixes for known vulnerabilities, so updating to them is sensible.
That can be difficult on a mature web application, though. Different versions of software are not always compatible with one another, so keeping things up to date and making sure everything works is not easy.
As these things are always changing, it is next to impossible to guarantee an application is secure. It may be that no one is aware of vulnerabilities in the latest version of your server software, for example. It is unlikely, though, that no flaws will be found in the future.
If you are worried about your website being hacked, you should read our article on website security for a few pointers.
Black Box vs White Box
There are different ways to conduct a vulnerability assessment on a website or application. One approach is to probe for vulnerabilities the same way a hacker would, with no inside knowledge or help. That is called black box testing.
White box testing, on the other hand, means security testing with access to information such as the source code of the application being probed or details about what software is being used.
The black box approach is more like what a criminal would do. Getting information about the system being tested is a key challenge for those using this method.
The white box strategy makes it easier to find vulnerabilities because the tester can browse through everything and see how it all fits together. If they know what software is running, they can target their attacks accordingly. That said, it may not indicate which vulnerabilities a real hacker would be likely to find.
Tools of the Pentest Trade
Linux is a popular operating system for those involved in security testing. If you need to do a vulnerability assessment on a website, Kali Linux is a particularly good distribution as it comes installed with all sorts of relevant software, including Wireshark and Burp suite, as well as many other useful tools.
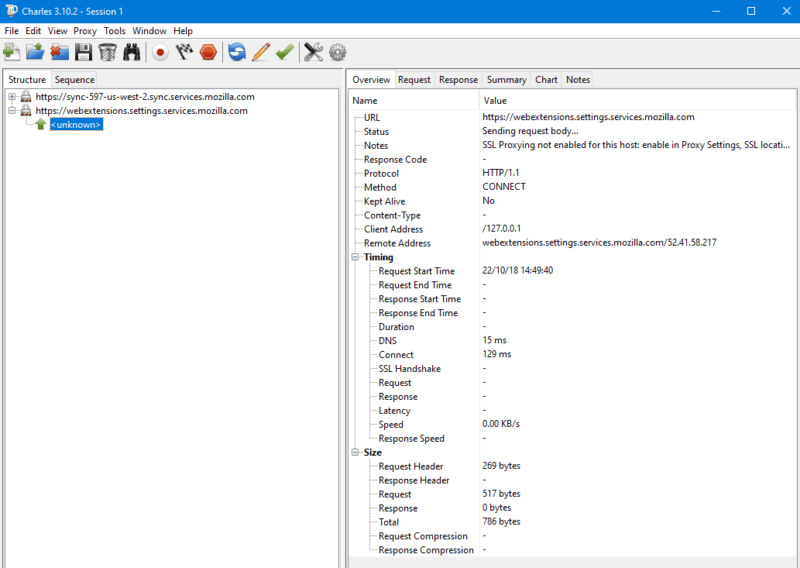
Using a tool such as Burp suite or Charles to monitor web traffic can give you a detailed picture of what is going on when you connect to a website. They monitor all the connections your computer makes and give you the details you need about them. They are also useful for regular web development and debugging.
You can use them to modify the requests that are sent, which is great if you want to see how a server responds to the kind of non-standard traffic that might come from a hacker.
There are also tools to automate brute force password attacks, which essentially try as many combinations as possible. It targets short, easy passwords. Using a password manager can help you generate longer ones that are less vulnerable to its assault.
Password forms are also a risk for SQL injection — sneaking code into the data passed to the server. A security tester can spot places where that could occur and update the code to ensure incoming data is handled safely.
Looking into how an application uses computer memory can also reveal vulnerabilities. Poking through the innards of an executable program can be done with the GNU debugger, or GDB. This kind of vulnerability testing involves looking for exploits that can give the hacker access to a shell and allow them to take control of a server.
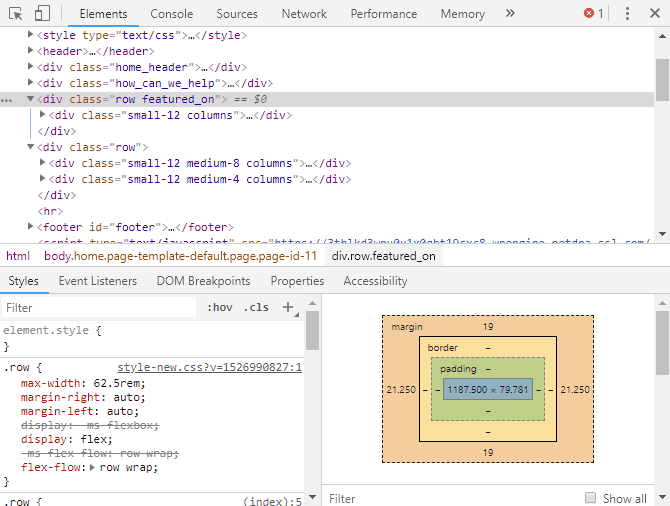
Most browsers have a dev console, which is also useful for examining what is happening on a website. Chrome’s dev tools will show what elements a page loads and reveal errors. In addition to causing problems for users, errors might leave a website vulnerable to attack.
You can find the dev console in Chrome by clicking the three dots at the top right to open the menu, then selecting “more tools” > “developer tools.” Click the “console” tab to view errors on the website you are looking at. You may be surprised to learn how much goes wrong, even on high-profile websites.
Some companies may use a virtual private network to help protect themselves from harm. An attacker can identify that, though, and a less secure connection may be vulnerable to exploitation. That is why it is important to be careful when picking a service and choose one of the best VPN providers around.
Making Money in Security Testing
If computer security interests you, it has never been easier to get involved. More companies than ever offer public bounties for those who find and report issues with their websites. Prizes can run as high as hundreds of thousands of dollars. Potential bounty hunters be warned, though, most are much lower and you’ll need to invest significant time if you want to land one.
That said, bag a few small prizes and you might be able to land a job as a security consultant, or penetration tester, teaching companies how to protect themselves from the less scrupulous bug hunters out there.
Final Thoughts
With an ever-changing digital landscape the need for security is the greatest it has been. Fortunately, awareness of the issues surrounding web application security, and security in general, has grown, too.
Penetration testing is a big part of security. It is a challenging field, but fascinating to study. If you’ve found this article useful, or have pentesting experience, let us know in the comments below. Thanks for reading.

