How to Detect a Stingray Device: Detection Apps & IMSI Catcher Protection Explained in 2025
Law enforcement uses StingRays, Hailstorms and other IMSI catchers to track mobile devices and capture data. In this guide, learn how to detect a StingRay device and keep your personal information secure.
If you’re concerned about surveillance, knowing how to detect a StingRay device is essential. StingRays trick your phone into connecting to them by mimicking real cell towers and then intercept your phone’s data. Using detection apps and a high-quality VPN can help secure your activity, but they won’t stop your phone from connecting to the device.
Spotting a StingRay can be tricky, but there are ways to protect yourself. Detection apps help identify fake cell towers, encrypted messaging apps keep communications secure and disabling 2G prevents forced network downgrades. In this guide, we’ll explain how StingRays work, which apps can detect them and the steps to take to secure your data.
-
02/20/2025 Facts checked
We’ve rewritten this article with the latest details and added information about detection apps and blocking methods.
What Is a StingRay Device?
A StingRay mimics a cell tower in order to intercept mobile device signals. When a mobile phone is nearby, it can unknowingly connect to the device, and the StingRay can collect data such as call logs, text messages and location information.

(Image Source: US Patent and Trademark Office)
Law enforcement agencies primarily use StingRays for surveillance and investigation, as they can track and monitor a suspect’s activity without their knowledge. However, StingRays can’t discriminate between connections — any cell phone within range can connect and sensitive data can be captured, posing a risk to your privacy.
Protect Your Privacy. Get Our Free VPN Guide Now!

- Comprehend the essential role a VPN plays in safeguarding your digital life
- Gain a deep understanding of how VPNs function under the hood
- Develop the ability to distinguish fact from fiction in VPN promotions
In 2015, a report by The Intercept revealed a leaked government catalogue detailing StingRay models and IMSI catchers. 10 The leak showed that law enforcement uses advanced devices capable of tracking phones, intercepting calls and potentially injecting spyware – and that the public are generally unaware of this kind of surveillance.
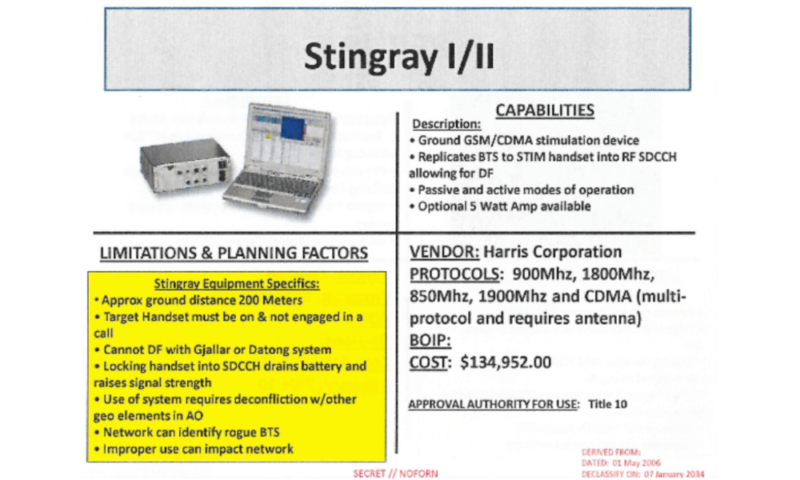
(Image Source: The Intercept)
StingRays are just one kind of IMSI catcher. IMSI stands for “international mobile subscriber identity” and refers to the unique number assigned to every mobile SIM card. Cellular networks use IMSI numbers to identify and authenticate users.
StingRay vs Hailstorm
StingRay and Hailstorm are similar devices created by the Harris Corporation. StingRay is the original cell-site simulator, working on 2G networks. Hailstorm devices are more advanced, and operate on 3G and 4G networks. 2 The majority of cell networks are 3G and 4G, so Hailstorm is more difficult to avoid. 9
Both types of IMSI catchers pose significant privacy concerns, but the original StingRay is much easier to detect and defend against than its Hailstorm counterpart. Hailstorm’s ability to bypass newer network security protocols makes it harder to effectively identify and block.
Are StingRay Devices Legal?
StingRay devices are illegal for most people, except for authorized entities, such as federal law enforcement and national security agencies. Such devices are typically used under strict oversight, and generally require a search warrant or court approval and the phone company’s cooperation.
Ongoing debates question whether StingRays violate the Fourth Amendment, which protects against unreasonable search and seizure. While reports suggest that agencies have used the devices without judicial oversight, courts have ruled in some cases that law enforcement must obtain a warrant before deploying such devices. 8
Criminals can also use StingRays. Hackers can obtain an IMSI catcher or even build their own device on a relatively low budget. 3 This constitutes unauthorized use with the intent to steal sensitive data — all the more alarming when you realize that cell phones connect automatically to cell-site simulators.
Who Uses Cell-Site Simulators?
Cell-site simulators like StingRays and Hailstorm devices are primarily used by government agencies and police forces in Canada, the U.K. and the U.S. However, it’s also possible for hackers or cybercriminals to use IMSI catchers to steal personal information.
Law Enforcement
Police departments have been known to use modern cell-site simulators to assist in criminal investigations. IMSI catchers can obtain a suspect’s general location when the target’s phone connects to the device. A warrant must be obtained before the device is used, except in exceptional circumstances.
The Department of Justice (DOJ) states that cell-site simulators do not function as GPS locators and must not obtain “the contents of any communication.” 5 This includes phone calls, SMS messages, images, emails and contact lists.
Intelligence Agencies
Agencies like the Federal Bureau of Investigation (FBI) use cell-site simulators for national security purposes. This can involve monitoring cell phones for potential threats or gathering intelligence from a target device.
Due to the sensitive nature of investigations, the use of cell-site simulators is often kept secret. This poses a privacy risk for nearby electronic devices belonging to innocent civilians, as these simulators can intercept data from cell phones belonging to people who have not been named in a search warrant or charged with a crime. 6
Unauthorized Actors
Hackers and cybercriminals can exploit IMSI catchers to steal personal information from unsuspecting individuals, though this is less likely due to the high price of legitimate cell-site simulators.
Rogue devices that mimic nearby cell towers can collect data from cell phones, including specific locations and the contents of phone calls and texts. This could lead to identity theft, fraudulent activity and financial losses.
StingRay Detection Apps
Most StingRay detection apps are outdated, poorly maintained or no longer functional – a lack of updates and support means they are unlikely to detect modern IMSI catchers. If you rely on these apps, understand that they may not work at all against newer surveillance technology.
Detection apps are primarily for Android devices; you won’t find many options for iOS. This is due to the level of access each operating system allows to its cellular network data. Android is much more flexible with its permission levels, whereas iOS has strict security measures to limit access to sensitive data.
Android IMSI Catcher Detector (AIMSICD)
AIMSICD is an open-source application for Android that works by monitoring your phone’s connection to cell towers and identifying unusual changes in network behavior. This phone app can alert you to sudden cell tower switches, signal downgrades (like a change from 4G to 2G) or irregular encryption levels.
This app is available only for Android phones and requires extensive device permissions to work effectively, including system and location data and access to the cellular network. AIMSICD works on both rooted and non-rooted devices, but its advanced features need root access for better detection accuracy.
Despite the benefits, AIMSICD has some limitations. It can produce false positives that identify legitimate networks as having IMSI catcher activity, and it isn’t regularly updated to maintain the best security and app function.
SnoopSnitch
SnoopSnitch is an IMSI catcher detector app for Android phones. However, the app needs a Qualcomm chipset to work properly, which limits its availability. See if your phone has this chipset by checking in the settings or searching online for the specifications. SnoopSnitch also requires a rooted device to access low-level network data.
To detect IMSI catchers like the StingRay, SnoopSnitch checks for unexpected signal downgrades, silent texts or connections to rogue cell towers that don’t belong to known carriers. You can also get security reports that explain potential threats and how to avoid them.
Darshak
Darshak detects IMSI catchers by monitoring and analyzing cellular broadcast messages. It checks for unusual behavior, like silent SMS messages (a signaling message that doesn’t pop up on your phone), sudden network downgrades or unexpected cell tower switches. If Darshak detects something, you’ll receive an alert that you may be in a StingRay area.
Darshak was developed for the Samsung Galaxy S3, but as it’s open source, it should work on any Android device running 4.1.2 or later. However, it’s not without limitations — it requires deep access to network data, which means you need to root your cell phone.
Rooting your device disables its inherent security measures, leaving it vulnerable to hacking and malware. As Darshak isn’t regularly updated, its outdated codebase could cause further vulnerabilities.
Crocodile Hunter
Crocodile Hunter is an open-source IMSI catcher detection tool developed by the Electronic Frontier Foundation (EFF).7 It’s not a mobile phone app, but rather a hardware-based tool that needs a laptop, a software-defined radio (SDR) and technical knowledge to operate. This makes it much less user-friendly than the apps listed above.
Crocodile Hunter can detect IMSI catchers by looking for unusual cell tower signals, such as network downgrades or very strong signals, and it can detect towers that don’t belong to legitimate network carriers. However, as of 2022, the EFF no longer officially maintains or updates Crocodile Hunter.
How to Block StingRay Surveillance
Blocking StingRay surveillance is tricky, but there are a few methods that help reduce the chances of your phone being tracked. Here are some of the easiest ways to avoid being caught by IMSI catchers.
Disable 2G
IMSI catchers will often force a phone to downgrade to a 2G network, as 2G has weaker (or sometimes nonexistent) encryption. You might be able to manually disable 2G connectivity in your phone’s network settings, but not all phones support this — some will let you disable only 3G or 4G.
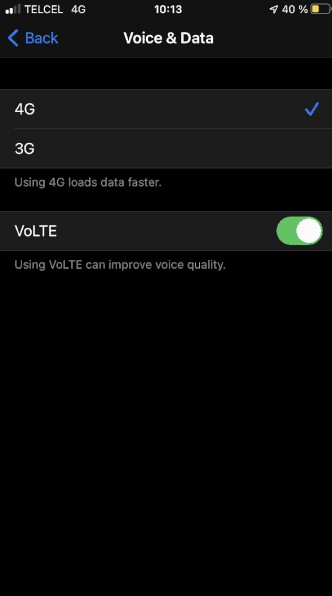
Bear in mind that StingRay technology is considered outdated, as many modern IMSI catchers now use 3G and 4G networks to capture data. A better option is to connect only to secure 5G networks, but this has its own issues — namely, many 5G networks are just faster 4G networks without improved security, and you can’t tell which is which.
Use Encrypted Communications
The main risk StingRay poses to your data is that the false cell tower captures information sent to and received by your phone, such as texts and phone calls. You can protect this data by using apps like Signal and WhatsApp, or iMessage and FaceTime on iOS.
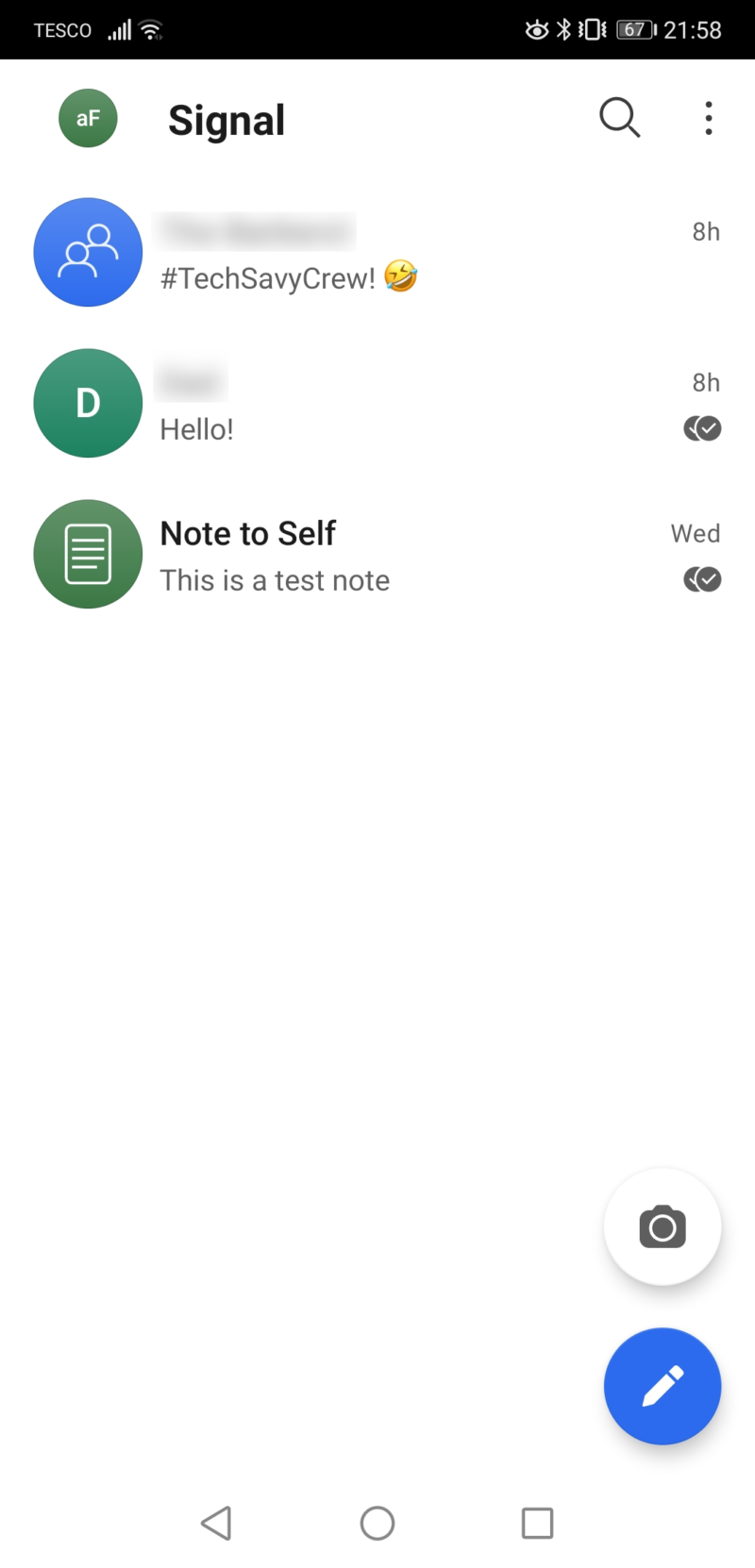
These messaging apps provide end-to-end encryption, so unauthorized third parties (such as StingRay operators) can’t access your data. The StingRay device can detect and capture your data, but encryption makes it unreadable. It doesn’t block StingRay connections entirely, but it does make your data significantly less accessible.
Use a Faraday Bag
A Faraday bag is a pouch that blocks signals and stops your phone from connecting to any network, including IMSI catchers. When your device is inside the bag, it is unable to communicate with any cell tower — even your regular phone network. The bag is lined with conductive materials that create a shield around your phone, blocking network signals.
A Faraday bag is a more foolproof option, but it limits usability. After all, when your phone is in the bag, you can’t make or receive calls or messages, and you’ll have no internet connection. High-quality bags can be expensive and, while there are other practical uses (like protecting payment cards while traveling), they’re not convenient for day-to-day use.
Can VPNs Protect You From StingRay Technology?
Yes, a VPN can help protect your data from being accessed by StingRays and similar IMSI catchers, but it won’t stop your phone from connecting to the cell-site simulator. When the device mimics a cell tower and your phone connects, your activity is intercepted. A VPN ensures traffic sent or received is undecipherable to whoever is capturing it.
A quality VPN protects your traffic by using secure encryption protocols to scramble your online data. A StingRay can tell that data is being transmitted, but the encryption prevents the data from being read. This also means a VPN can protect you from hackers co-opting IMSI catcher technology.
If you’re looking for a VPN to protect your phone, check out our NordVPN review and Surfshark review. Importantly, VPNs don’t secure regular text messages — make sure you’re using a secure messaging app like WhatsApp or Signal. VPNs also don’t stop StingRays from tracking your general location.
IMSI catchers detect signal strength, which can be used to estimate where you are. This occurs on the cell network level, and your VPN cannot block or mask it.
Final Thoughts
Protecting your phone from StingRays is challenging, but there are ways to secure your data. However, no single method is foolproof, so it’s best to use several methods combined. The strategy of disabling 2G networks, using encrypted apps and connecting to a VPN works well.
Do you think law enforcement should have to disclose when and where they use StingRays? Have you tried using an IMSI catcher detection app? Which other privacy tools do you use to protect your data? Let us know in the comments, and thank you for reading.
FAQ: StingRay Device Blocker
Generally, StingRays are not legal for private citizens to own. They are powerful surveillance tools that are authorized for use only by law enforcement officials.
A StingRay looks like a small cell tower, with multiple connections for different antennas. Usually the device is small — the size of a small laptop or briefcase — making it portable.
Yes, a VPN can protect against StingRays to an extent. While it cannot stop cell phones from connecting to the false cell tower signal, a VPN encrypts the data sent from the device. The encrypted data will be unreadable to whoever is using the StingRay.
Local police departments and federal law enforcement agencies use StingRays and other IMSI catchers to track cell phones and capture data from them. The devices are used as part of authorized surveillance operations.
Sources:
- How Cops Can Secretly Track Your Phone – The Intercept
- Stinging Back: Resisting Government Surveillance of Cellphones – Criminal Legal News
- With $20 of Gear from Amazon, Nearly Anyone Can Make This IMSI-Catcher in 30 Minutes – Vice
- H.R.3871 – To amend title 18, United States Code, to regulate the use of cell-site simulators, and for other purposes. – Congress.gov
- Department of Justice Policy Guidance: Use of Cell-Site Simulator Technology – Justice.gov
- Federal Recommendations on the Use of Cell Site Simulators – ACLU
- Crocodile Hunter – Electronic Frontier Foundation
- State of Maryland v. Kerron Andrews – Electronic Frontier Foundation
- The Mobile Economy 2024 — GSMA
- Stingrays: A Secret Catalogue of Government Gear for Spying on Your Cellphone — The Intercept


