Amazon Virtual Private Cloud: Definition, Features, How It Works, Use Cases and Pricing
Amazon Virtual Private Cloud is an essential layer of security in the AWS cloud, as it prevents unauthorized access while providing consolidated network management. In this article, we talk about its features, working mechanism, components, use cases and pricing.
Amazon Virtual Private Cloud (VPC) is a service that creates a logically isolated network in AWS. It offers a form of security for cloud computing resources, as it prevents just anyone from having access. AWS VPC offers traffic mirroring, security groups, network access control lists, IP addressing, network managers and flow logs, among other features.
Think of it as a well secured network environment within Amazon Elastic Compute Cloud, or any other Amazon based cloud service, such as AWS Elastic Beanstalk.
AWS Virtual Private Cloud allows you to create a virtual network similar to a physical network in a data center. It lets you control the IP address, security, subnetting, traffic and so on, isolating the network as needed.
Creating an AWS VPC primarily involves defining an IP address range (a CIDR block) and creating a private or public subnet. Depending on the architecture of your cloud environment, you may also set up endpoints and gateways when creating the VPC.
You can use AWS VPC for simple websites, but if you really want to put it to work, use it for multi-tier web applications or when creating a hybrid cloud environment.
Amazon VPC itself comes at no extra charge. However, components like network address translation (NAT) gateways, public IP addresses and IP address managers are charged at an hourly rate. We’ll cover all of this in our guide, and you can get a broader view of the AWS resource hierarchy here.
-
11/19/2024
Updated article with important key takeaways.
What Is Amazon Virtual Private Cloud (AWS VPC)?
Amazon’s virtual private cloud service, AWS VPC, offers an isolated network in the AWS public cloud environment. It is an example of a private cloud deployment but can also be considered a hybrid cloud deployment since it features the scalability of the public cloud. AWS VPC virtual networks are like physical networks, but they come with the added advantages of flexibility and scalability.
An AWS VPC can be either private or public depending on the internet access. When private, the VPC does not have a public subnet, which is a subnet associated with an internet gateway. However, public VPCs do have public subnets.
The core purpose of an AWS VPC is logical isolation: It isolates your resources in AWS, preventing unauthorized network access. In addition to isolation, it lets you manage communication among the resources in the VPC and with the internet.
What Is Default AWS VPC?
When you create an account, Amazon Web Services (AWS) creates a default VPC for your account in all AWS regions. With this, you can launch AWS resources and build your cloud infrastructure right away.

into using AWS without having in-depth networking experience.
AWS’ default VPC is public since it comes with a public subnet in each region’s availability zone. When you launch AWS resources like EC2 instances in a default VPC, they get a public IP address.
Of course, the public subnet in a default VPC connects to the internet through an internet gateway, so every default VPC has an internet gateway. Default VPCs also come with access control lists (ACLs) and security groups, which control traffic to and from the network.
The upside of default AWS VPCs is the simplicity and ease they offer first-time users, particularly beginners. Instead of worrying about the intricacies of configuring a VPC, they can jump into deployment straight away.
What Is a Non-Default AWS VPC?
A non-default AWS VPC is basically a custom VPC — it does pretty much the same thing as a default VPC, but you tweak it to your taste.
Non-default AWS VPCs give you a high level of control over your network, allowing you to configure the IP address range, security group, access control list (ACL), route table, public or private subnets and so on. For internet or external network access, they may also have gateways and endpoints.
The upside of non-default AWS VPCs is that they can offer more security than a default VPC if configured correctly.
What Are the Features of AWS VPC?
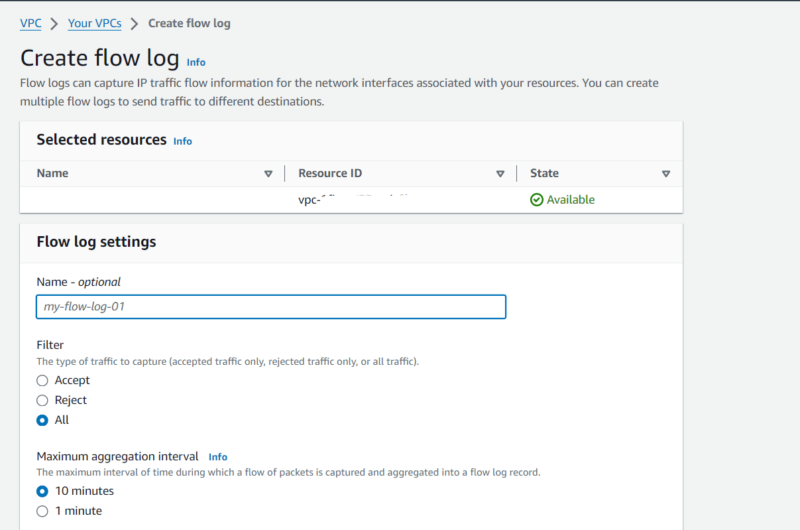
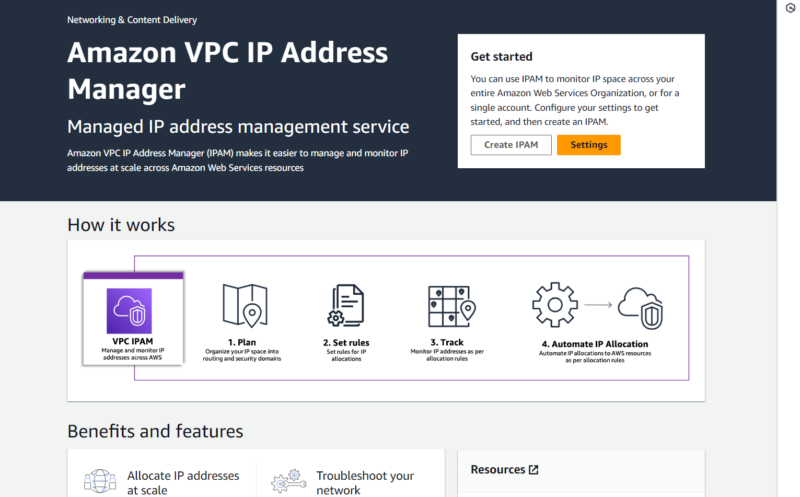
The main features of AWS virtual private clouds are flow logs, the IP address manager (IPAM), IP addressing, ingress routing, the network access analyzer, the network manager, network access control lists, the reachability analyzer, security groups, traffic mirroring and lattice. Each feature helps increase security in different ways, which we discuss in detail below.
How Does AWS VPC Work?
AWS VPC works by creating a virtual network that is cut off from other virtual networks in AWS. This ensures the resources and data in each account are secure and private.
For efficient routing and organization, VPCs are grouped into subnets, which are smaller networks within the larger virtual network. The subnets can be either private or public; public subnets having direct internet access, while private subnets don’t.
A public subnet in an AWS VPC connects to the internet through the VPC’s internet gateway. That said, you can also make resources in a private subnet internet accessible using a NAT gateway or a NAT instance.
VPCs have an IP address range (also known as a CIDR block), which defines the possible addresses of the resources within the network. The subnets also have IP ranges that fall within the VPCs’ IP address range.
Network access control lists (ACLs) and security groups are some components with which VPCs secure their resources. Though both have similar traffic control functions, their scope and usage differ. For one, ACLs control traffic into the subnets, while security groups control traffic into the resources.
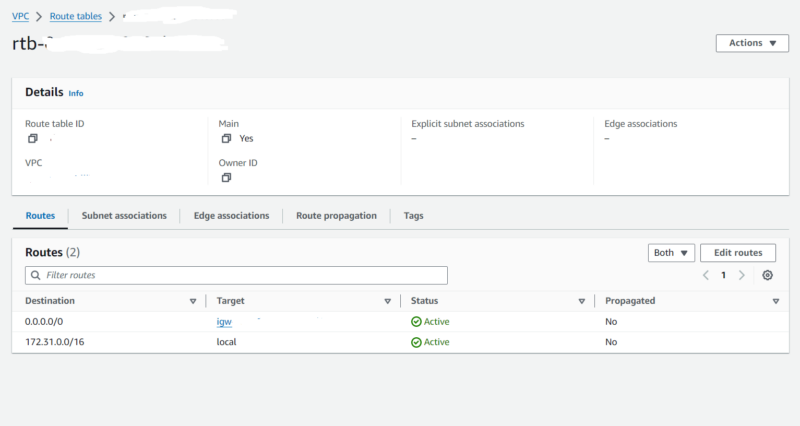
Route tables determine the direction in which traffic flows within a VPC. They contain a table of target IDs matched to destination IP addresses. This matching means that traffic to a destination IP address is directed to the target resource with the specified ID.
What Is the Architecture of AWS VPC?

AWS VPCs are regional services; they act as the container for all the resources and network components in a specific region in an AWS account. They are subdivided into subnets, which can exist in one or more availability zones.
When not associated with an internet gateway, the subnets are private. However, when they are associated with an internet gateway, the subnets are public, meaning they have internet access.
Basic VPC architecture includes a route table, security group and network access control list. The route table describes the direction of traffic from a subnet, while the security group and network ACL secure the VPC’s resources. The security group acts as a stateful firewall for resources within a subnet, and the network ACL is like a stateless firewall for subnet traffic.
Depending on your needs, an AWS VPC’s architecture may also include endpoints, peering connections, NAT gateways, carrier gateways, site-to-site VPN connections and more.
What Are the Components of AWS VPC?
The main components of AWS VPC are subnets, route tables, internet gateways, network ACLs and security groups. We discuss the roles of these components below.
What Is a Security Group in AWS VPC?
A security group in AWS VPC is the firewall of a VPC’s resources. It contains rules that control the flow of network traffic to and from the resources.
Security groups control traffic based on protocol, source and port range. In other words, a security group can allow or deny network traffic based on the network protocol, port or source of the traffic. The source identifier can be an IP address, an IP address range or a security group ID.
When using security groups, we can specify different rules for inbound and outbound connections. That said, security groups are stateful; they allow for return traffic for each connection. Unlike security groups, access control lists are not stateful.
You can associate multiple security groups with a resource. Similarly, you can associate multiple resources with a security group.
In default VPCs, security groups allow all outgoing connections but restrict all incoming connections. However, you can update the security group in a default VPC to allow incoming traffic as needed.
What Is AWS Private Global Network?
AWS Global Network is a service that consolidates networking infrastructure across multiple environments, including AWS and on-premises networks. Think of it as a container for networks that you would normally manage separately. AWS global networks come in handy when dealing with complex networks across multiple regions or accounts.
AWS Global Network promotes visibility by providing a dashboard with geographic and topological representations of the network objects. It also enables centralized management with multi-account monitoring systems and consistent access policies.
Though it offers some management functions, AWS Global Network cannot modify network resources such as virtual private clouds (VPCs). You have to modify said resources following the usual steps.
How Do AWS VPCs Access the Internet?
VPC resources access the internet directly using their internet gateways. At the same time, incoming internet traffic gains access to the VPC through the internet gateway. Of course, both incoming traffic and outgoing traffic are subject to the rules of the security groups and access control lists.
Apart from an internet gateway, VPC resources can access the internet using a NAT gateway. NAT gateways are a network translation service that routes traffic from resources in a private subnet to the internet.
NAT gateways exist in public subnets and serve as an intermediary between private subnets and the internet. They’re the better option when you want your private subnet to retain its privacy while having access to the internet.
In place of NAT gateways, you can use NAT instances, which are public EC2 instances that route traffic from private subnets to the internet using IP forwarding.
What Are the Methods to Create and Manage AWS VPCs?
The main methods to create and manage an AWS virtual private cloud are the AWS management console, AWS SDK, the AWS command line interface (CLI) and the query API. Here’s how each one works:
How to Create a VPC Using AWS CLI
To create a non-default AWS VPC from the CLI, run the aws ec2 create-vpc command. When running the command, you may specify one of many options to customize the VPC. Some of those options include the following:
- –cidr-block: Use this option to specify the IPv4 address range of the VPC.
- –region: This option defines the region in which you create the VPC.
- –ipv4-ipam-pool-id: Specify an IPAM pool ID when you want to use the CIDR from an IPAM pool.
Besides the VPC itself, you can create subnets, route tables, routes, internet gateways, security groups and network ACLs from the command line. Here’s a list of the commands and their corresponding components:
- aws ec2 create-subnet creates subnets.
- aws ec2 create-route-table creates route tables.
- aws ec2 create-route creates a route in a route table.
- aws ec2 create-internet-gateway creates an internet gateway.
- aws ec2 create-security-group creates a security group.
- aws ec2 create-network-acl creates a network access control list.
There are CLI commands for many other VPC components, but we only listed the most essential ones here.
How to Manage a VPC Using AWS CLI
The AWS CLI can manage a VPC using various commands, including the following:
- aws ec2 delete-vpc deletes a VPC.
- aws ec2 associate-vpc-cidr-block associates an IP address range with a VPC.
- aws ec2 create-default-vpc creates a default VPC.
- aws ec2 disassociate-vpc-cidr-block removes an IP address range from a VPC.
- aws ec2 modify-vpc-endpoint changes attributes of a VPC endpoint.
- aws ec2 allocate-ipam-pool-cidr allocates CIDR blocks from an IPAM to another IPAM pool or resource.
What Are the Use Cases of AWS VPC?
The main use cases of AWS Virtual Private Cloud are securing simple websites and blogs, creating hybrid connections and hosting multi-tier web applications. Here’s how AWS VPC makes these use cases possible:
- Securing simple websites and blogs: Using security groups, AWS VPC controls traffic to and from a server in a subnet. This ensures such websites or blogs have appropriate security positioning.
- Creating hybrid connections: With VPC components like Site-to-Site VPN and AWS Direct Connect, you can readily connect a VPC to on-premises infrastructure, creating a hybrid cloud environment.
- Hosting multi-tier web applications: When dealing with multi-tier web applications that have sensitive resources, like databases, ensure such resources are restricted from public access. At the same time, you want to ensure that public resources remain public. VPCs make this possible with security groups, private subnets and public subnets.
What Is the Pricing Structure of AWS VPC?
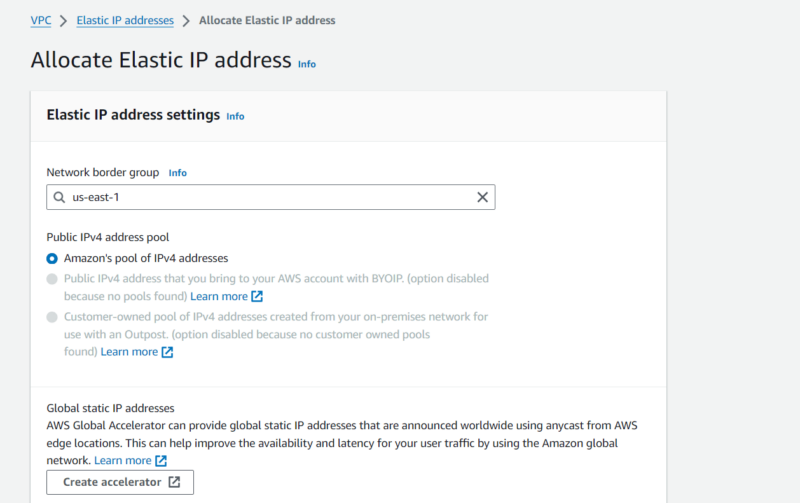
AWS VPC comes at no extra cost. However, you’ll accrue charges for components like the NAT gateway, public IPs, the IP address manager, traffic mirroring, the network access analyzer and the reachability analyzer.
The IP address manager, the NAT gateway, traffic mirroring and public IPs have hourly rates. However, the network analysis components (network access analyzer and reachability analyzer) are charged per analysis.
What Are the Alternatives to AWS Virtual Private Cloud?
The main alternatives to AWS Virtual Private Cloud are Microsoft Azure Virtual Network, Google VPC, DigitalOcean Virtual Private Cloud and IBM Cloud VPC. Here’s how each one compares to AWS VPC.
- Google VPC: Like AWS VPC, Google Cloud VPC creates isolated virtual networks on the Google Cloud Platform (GCP). However, it is global, not regional like AWS VPC. In addition, subnets in Google VPC are regional, not zonal like AWS.
- Microsoft Azure Virtual Network: Microsoft Azure Virtual Network provides logically isolated networks in the Microsoft Azure public cloud infrastructure. Azure Virtual Network’s seamless integration with active directory streamlines access management for the virtual network.
- DigitalOcean Virtual Private Cloud: DigitalOcean Virtual Private Cloud offers the same primary purpose as AWS VPC. However, DigitalOcean Virtual Private Cloud offers a simpler interface and may not scale to the same extent as AWS VPC.
- IBM Cloud VPC: IBM Cloud VPC creates virtual networks in IBM Cloud. Though similar to AWS VPC, it offers better support for bare-metal servers.
What Is the Main Difference Between VPC and Private Cloud?
The main difference between VPC and a private cloud is that a VPC represents a virtual network, while a private cloud is a cloud computing deployment model.
VPCs are virtual versions of physical networks isolated from the internet. Since they are virtual resources, you do not have control over the underlying hardware. However, you have a high degree of control over the network configuration.
On the other hand, when running a private cloud, you typically have total control of the underlying infrastructure, except for the management and maintenance, which are outsourced. That said, a VPC is primarily considered a form of private cloud.
What Is the Main Difference Between a VPC and a VPN?
A VPC is an isolated virtual network in a public cloud. It offers privacy, security and scalability while streamlining network management in the cloud.
On the other hand, a VPN, or virtual private network, is a secure tunnel between computing devices or networks on the internet. VPNs ensure secure data transfer, as they provide a private, encrypted route for data being sent over the internet.
Final Thoughts
AWS VPC facilitates network privacy and security in AWS Cloud, while its subnets ensure logical segmentation of your resources. If you’re looking to extend your public cloud resources to an on-premises environment, AWS VPC components like Site-to-Site VPN and Direct Connect simplify the process.
What has your experience been like with AWS VPC? Did we overlook anything you wanted us to discuss? We’d love to hear from you, so leave a comment below. As always, thank you for reading.
FAQ: Virtual Private Cloud (VPC)
Amazon Virtual Private Cloud is an isolated virtual network deployed to an account in the AWS public cloud computing platform.
A VPC in AWS is a service that creates isolated virtual networks in your account.
Amazon Virtual Private Cloud is best described as a service that creates non-overlapping virtual networks in the AWS public cloud.
Yes, Amazon offers private cloud services. Some of its offerings include AWS Direct Connect and Site-to-Site VPN.